Welcome to the third session of Ironcore’s Zero Trust educational series, Zero Trust – Endpoints.
Zero Trust cyber security is a fundamental change in the way that cyber security defenses operate, and build on traditional cyber defenses of the past. Zero Trust Cyber Security services provide layers of protection for six different areas: Data, Identities (Users), Endpoints, Applications, Network, and Infrastructure. These layers are designed to together, each one specifically engineered to prevent unauthorized access within different components of your network.
One of the goals of this series is to familiarize you with the scope and extent of Zero Trust and how it would provide additional protection from cyber threats. We do not expect that you’ll become a Zero Trust expert, but we believe that understanding the basics of Zero Trust will be to your organization’s benefit when talking to examiners, auditors, and cyber insurance agents.
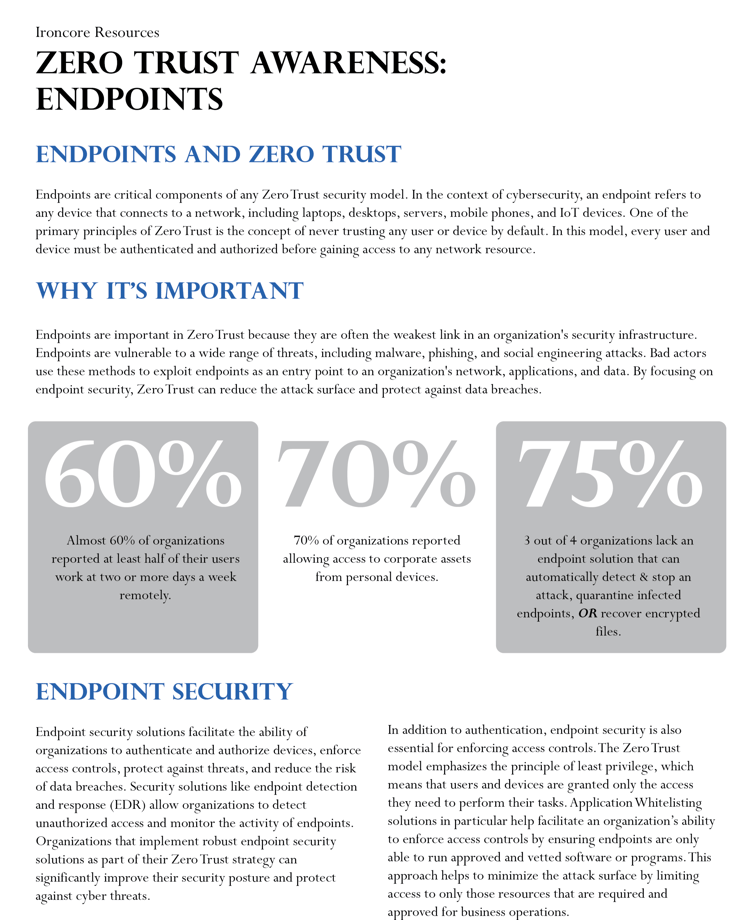
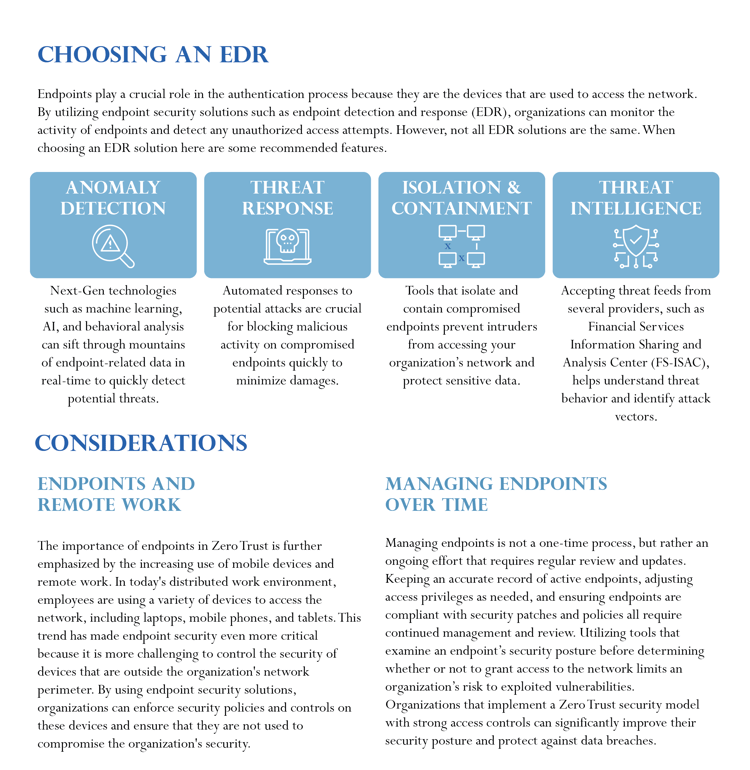
Much like our last Zero Trust topic; identity, endpoints such as PCs, laptops, and mobile devices should be granted access to your network only after they have been authenticated and authorized. Endpoints are important in Zero Trust because they are often the weakest link in an organization's security infrastructure with vulnerabilities to a wide range of threats; including malware, phishing, and social engineering attacks. Additionally, today’s distributed work environment makes endpoint security especially important, as managing the variety of devices employees utilize for network access becomes more complicated. In this session, we discuss how organizations are able to limit network access to only authenticated and authorized devices, enforce access controls, protect against threats, and reduce the risk of data breaches with Zero Trust security practices.
Click here for a printable version of this flyer.
Our Zero Trust series is available to you and anyone else in your organization. We encourage you to share this information with anyone inside or outside of your organization that may benefit from this series.
If you have any questions about what you see here, please feel free to contact us at zerotrust@ironcore-inc.com. We will be happy to provide additional information.

