You may have heard the phrase, “Zero Trust Cyber Security” recently. However, most people outside of cyber security professionals, don’t really understand what this means. Ironcore would like to help change that.
As cyber criminals become more and more creative and destructive with their attacks, traditional methods of preventing, identifying, and mitigating these attacks need to change to meet this challenge. Zero Trust cyber security tools and services is the evolutionary change in cyber fighting that will be required to accomplish this.
The first step to move your organization to a Zero Trust position is to understand what Zero Trust tools do, where they need to be put in place and how they protect your organization from these new, more sophisticated cyber-attacks.
To assist you and your organization to better understand these new Zero Trust tools and services, Ironcore has designed a series of six, non-technical, educational sessions that will cover the six areas requiring Zero Trust; Data, Identities, End Points, Applications, Network, and Infrastructure.
Beginning with Zero Trust-Data, about once a month, Ironcore will publish a blog that discusses one of the above six Zero Trust focus points and explains how the Zero Trust philosophy better protects your organization from a successful cyber-attack.
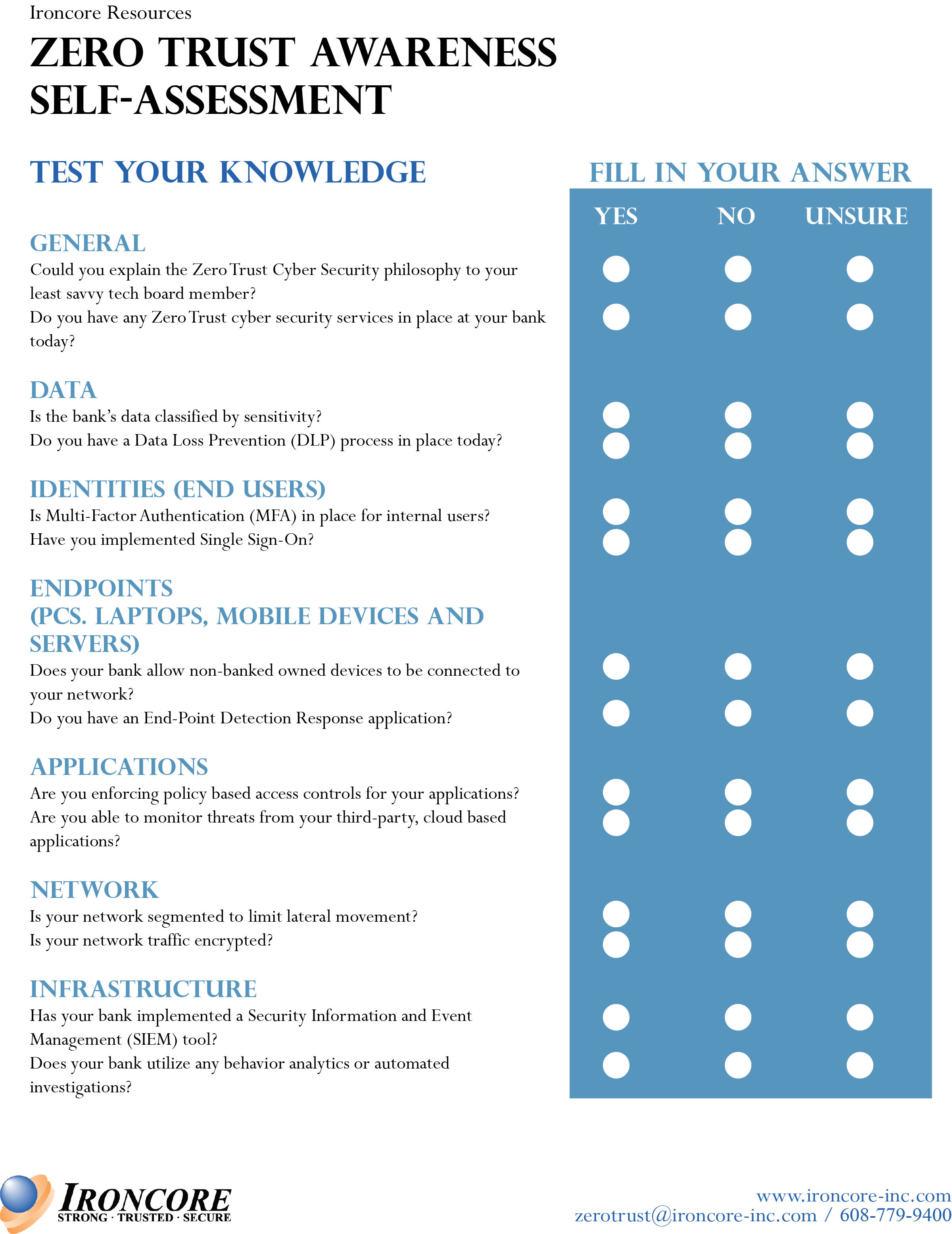
In the meantime, included in this blog post is a Zero Trust awareness self-assessment that you can use to gauge your current knowledge of Zero Trust and why it is important. (Unlike the FFIEC CAT and the R-SAT, this truly is voluntary). We would encourage you to complete this assessment now and put it aside for the time being. At the end of the educational series, we will provide the same self-assessment for you to complete again. Hopefully, by the end of this series, you will feel much more confident about your understanding of the Zero Trust cyber protection philosophy.
Click here for a printable version of this assessment.